Technical System Landscape
Sinch Contact Pro provides its users with advanced telephony and contact center features.
The figure below shows an overview of the technical system landscape of Sinch Contact Pro.
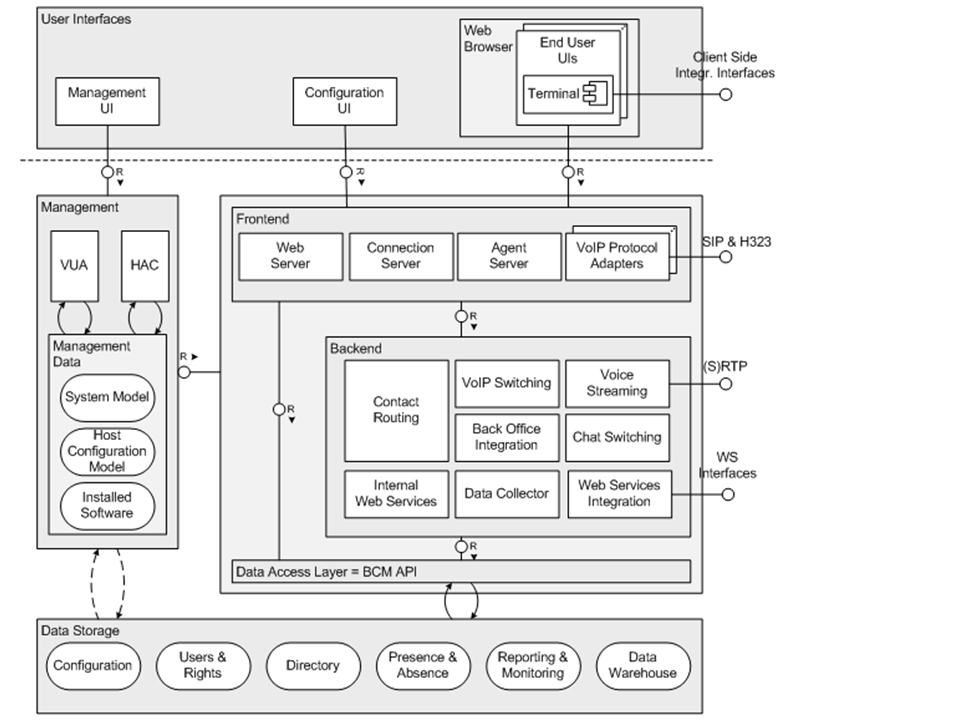
The system utilizes VoIP technology, but it is not internet telephony. The system is basically set up either of the following two alternatives:
-
On-premise system, where all equipment and consequently all related IP traffic is in the enterprise LAN.
-
Software as a Service (SaaS) where only the terminals are in the enterprise LAN and the service is provided by an application service provider (ASP).
Violations against both of these are possible and they are possible for traditional telephone systems as well. With an on-premise system, an intruder has to break into the enterprise LAN, with an ASP system either to the enterprise or an ASP LAN.
In the latter case, a secure IP connection, for example a VPN or leased line, must be established between the ASP and the enterprise. Firewalls may exist on either or both ends of the connection. With the ASP system you gain the major benefit of having trained and experienced professionals to take care of technical and operational issues, such as back-up power, security and overall maintenance of the system.
In both cases, external calls are routed over the traditional telephone network. The VoIP stream is terminated in the LAN at a VoIP gateway, which transfers the information to suitable format for the telephone network. The gateway is connected to a telephone exchange via a traditional PRI (E1/T1/J1) line, similar to those connecting PBXs to the telephone network.
The main security issues are:
-
Confidentiality, can your communications be monitored or your passwords be exploited.
-
Integrity, can signaling information be falsified or system setup be modified for unauthorized purposes.
-
Availability, is the system available when you need it.
-
Traceability, the software collects data for enabling the services and related invoicing, security and troubleshooting, protecting the services against misuse and misappropriation, and further improvement of the software and services.
-
Legal, supervisory and contractual obligations must be fulfilled.
