Configuring Mail Server for Server Authentication
To configure MS365 as mail server, System Configurator configuration requires Application registration ID. Follow the steps below to register application at Azure Active Directory (AD).
Register Application
Register the application with your Azure Active Directory tenant. Some registration is required for Microsoft to act as an authority for your application.
Configure Application
- Choose the Azure AD tenant where you want to create your applications.
- Sign in to the Azure portal.
If your account is present in more than one Azure AD tenant, select Directory + Subscription, which is an icon of a notebook with a filter next to the alert icon, and switch your portal session to the desired Azure AD tenant.
- Select Manage Azure Active Directory.
- Select App registrations.
- Register the client app:
- In the App registrations page, select +New registration.
- When the Register an application page appears,
enter your application's registration information:
- In the Name section, enter a meaningful application name. This is not used in System Configurator.
- In the Supported account types section, select an option that suits your purposes.
- No need to specify Redirect URI since it is not used in this case.
- Select Register to create the application.
- On the app Overview page, find the following values and
copy them:
- Application (client) ID
- Directory (tenant) ID
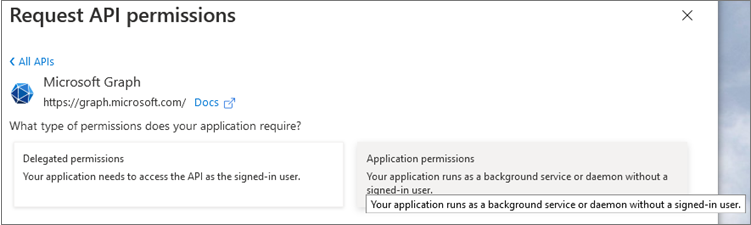
- Click the View API permissions button or API
permissions left navigation item.
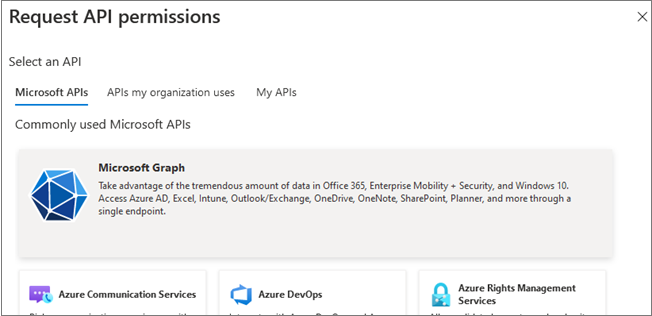
- Click the Add a permission button and then ensure that the Microsoft APIs tab is selected (by default, it is selected).
- In the Commonly used Microsoft APIs section,
click on the Microsoft Graph.
-
In the Application permissions section, ensure that the right permissions are checked: Mail.ReadWrite. (Mail.Send if you are going to use MS365 as an outgoing mail server.) Use the search box if necessary.
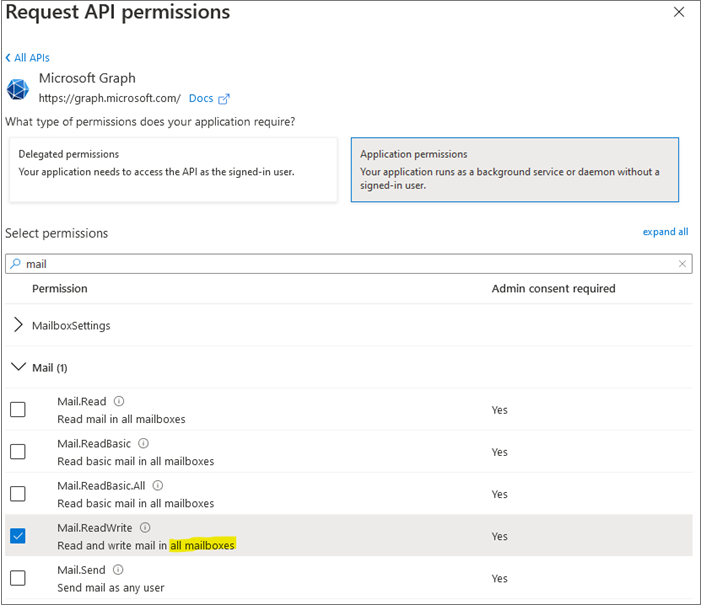 Note:Pay attention to the text describing permission Mail.ReadWrite - Read and write mail in all mailboxes. These are very powerful permissions. The section Granting Permissions to Access Mailboxes tells how to limit application access to specified mailboxes.
Note:Pay attention to the text describing permission Mail.ReadWrite - Read and write mail in all mailboxes. These are very powerful permissions. The section Granting Permissions to Access Mailboxes tells how to limit application access to specified mailboxes. - Select the Add permissions button. Permissions are now assigned correctly but the client app does not allow interaction. Therefore, no consent can be presented via a user interface and accepted to use the service.
- Click the Grant/revoke admin consent for [tenant] button, and then select Yes when you are asked if you want to grant consent for the requested permissions for all accounts in the tenant. You need to be an Azure AD tenant admin to do this.
- In the left navigation pane, select Certificates & secrets.
- Add the application password. The Sinch Contact Pro application will use this
password to authenticate and request OAuth token at the MS365 Mail Server.
- Click New client secret.
- Specify description. This is not used by Sinch Contact Pro.
- Select expiration. If you choose a secret that expires in the future, you must repeat these steps when the secret expires.
- You will be shown an ID and value. Copy the value field. You will not be able to retrieve it in the future. You get more information from the information message at the top of the page.
Azure AD configuration is completed.
