Group Managed Service Accounts (gMSA)
Use
As of SP09, it is possible to use Group Managed Service Accounts (gMSA) for running High Availability Controller (HAC), Alarm Server, web-related processes, and SQL services.
Using gMSA enhances security in Sinch Contact Center because:
-
gMSA accounts have an automatically renewed password with 120 characters
-
they cannot perform interactive logons.
We support using gMSA accounts with Windows Server and domain version 2012/2012 R2, and Windows SQL 2012, or later.
Cloud and On-Premise
gMSA can be used both in on-premise and cloud systems. In cloud, or any multi-tenant system, use for the SQL system administrator an account separate from the customer-specific account, and use the latter for running customer-specific services and connecting to customer-specific databases.
In one-customer-on-premise system one account can be used.
Limitations
-
SQL Reporting Services and Analysis Services (the account configured in SQL Reporting Services Configuration Manager, see Configuring Reporting Services) cannot use gMSA accounts.
-
gMSA accounts cannot be used as ODBC credentials for OLAP/WDU databases, that is, to access data sources as required by the Contact Log report in Standard Reports installation variable Windows User Account for Data Sources.
-
gMSA account cannot be used for SQL authentication because the password cannot be entered manually.
-
At the moment Microsoft tools do not support changing the gMSA account if you have once assigned it to a service. If you for any reason need to change the account, you must use an appropriate command on command line, such as sc config "SERVICE NAME" obj= <DOMAIN\GMSA ACCOUNT>. See Microsoft documentation about gMSA for any updates on the issue.
Note that Managed Service Account (MSA) cannot be used as its use is limited to one server.
Procedure
Create and Configure gMSA
-
To install the appropriate tools of Windows Server locally on all servers of the system and also on the AD server: choose from Server manager the following options:
-
: Role based or feature based installation, then click Next.
-
Server selection: Select server from the server pool, then click Next.
-
Server Roles: click Next.
-
Figure 1. Installing Windows Administration Tools 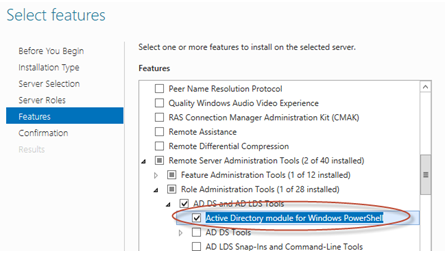
-
-
Configure the group key distribution service. Run this Power Shell command once in the domain: Add-KdsRootKey -EffectiveTime ((get-date).addhours(-10)).
-
Create a user group of the type
Security Group
for each customer system. Use group name that refers to gMSA and the customer, for example ACME_gMSA_Servers. -
Add Computers to the list of Object types, and if gMSA is used for HAC and the install media uses the UNC path, add all relevant servers to the above-mentioned user group in AD console.
Figure 2. Adding Computers Object Type 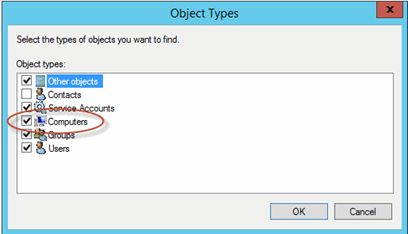
-
Create the gMSA account for each customer system, and grant it rights to the user group above. For information, see https://technet.microsoft.com/en-us/library/hh831782.aspx
-
Maximum length of the account name is 15 characters.
-
Use customer name or identifier in the account name, for example ACME_gMSA.
-
-
Reboot all servers.
-
Enable account on relevant application servers.
For example, use the short command in Power Shell command line Install-ADServiceAccount ACME_gMSA
-
Add the account (ACME_gMSA) to local admin group on relevant servers.
-
To create a separate gMSA account for SQL system administrator, repeat the steps 3 – 8:
-
Step 3: Create a user group of the type
Security Group
, for example SQL_gMSA_Servers. -
Step 4: Add the SQL server to the above-mentioned user group in AD console.
-
Step 5: Create the gMSA account, for example SQL_gMSA, and grant it rights to the user group above.
-
Step 6: Reboot SQL server.
-
Step 7: Enable account on SQL server. For example, use the short command Install-ADServiceAccount SQL_gMSA
-
Step 8: Add the account (SQL_gMSA) to local admin group on SQL server.
-
Assign gMSA to SQL Service
In Windows Services list, set the SQL service and SQL server agent to use the SQL_gMSA account.
Assign gMSA to Sinch Contact Center system
-
Assign the customer-specific gMSA ACME_gMSA account to all of the following services. Using different accounts in different parts of the system may lead to malfunction.
-
Make sure you have proper gMSA accounts defined and that you use its account name. IA cannot check if gMSA exists. If the option Use Group Managed Service Account (gMSA) is selected in an installation package, the password cannot be entered.
-
In IA, enter gMSA account name for database user account in variables of Configuration Database Server and other database servers, also Reporting Database Server.
-
In IA,
-
check the Use Group Managed Service Account (gMSA) checkbox, and
-
enter the gMSA account name to the variable where account name is asked,
in the following software packages:
-
For HAC service: HAC Service Logon User Account, see Creating HAC Nodes and Starting HAC Services.
-
For Alarm Server: Alarm Service Logon User Account service account, see Alarm Server Variables.
-
For Chat Portal Server, Integration Interfaces, and Web Server: Windows User Account for Running Web-Related Processes, see Web Server Variables, Chat Portal Server Variables and Integration Interfaces Variables, accordingly.
-
